DynELF Illustrated
I recently read this blog post about how the DynELF class from pwntools does what it does (which is resolving functions using info leaks).
The blog post does a very nice job describing this complex process but I think a drawing would help in understanding…a picture says more than a thousand words, right?
So I decided to hack up a program that uses the ptrace system call to attach to a process and dump the relevant data structures in dot notation. See it below.
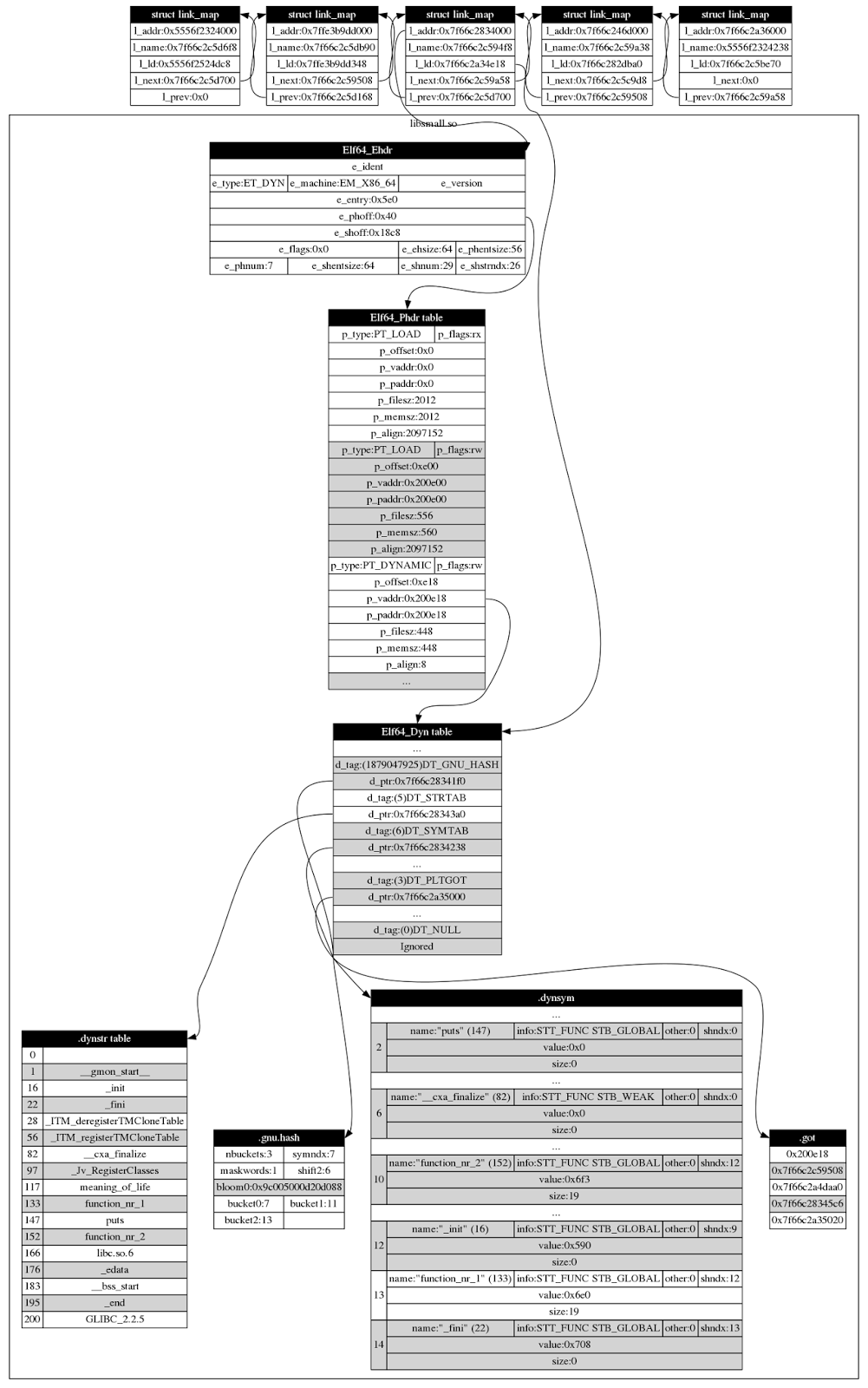
I only dumped details about one loaded library, namely the one called libsmall.so because these structures are quite large so to keep the illustration small this was the compromise.
The code for libsmall.so can be seen here:
#include <stdio.h>
void function_nr_1() {
printf("function_nr_1\n");
}
void function_nr_2() {
printf("function_nr_2\n");
}Since the original post did so well explaining I will not repeat it.
The first linkmap structure points to the main program, the next points to the vDSO. Then comes the libsmall.so followed by libc.so and the linker.
I hope this helps in understanding this exciting topic.